- News
Subscribe to our newsletter to receive the same news by email:
Changes and updates
Fixed problems
- Fix automatic upgrades aborting with the error message "
The upgrade could not be downloaded" even after a successful download. (#20593)
For more details, read our changelog.
Get Tails 6.9
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 6.0 or later to 6.9.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 6.9 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 6.9 directly:
This release is an emergency release to fix a critical security vulnerability in Tor Browser.
Changes and updates
Update Tor Browser to 13.5.7, which fixes MFSA 2024-51, a major use-after-free vulnerability. Using this vulnerability, an attacker could take control of Tor Browser, but probably not deanonymize you in Tails.
Mozilla is aware of this attack being used in the wild.
Fixed problems
For more details, read our changelog.
Get Tails 6.8.1
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 6.0 or later to 6.8.1.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 6.8.1 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 6.8.1 directly:
New features
File system repair when unlocking the Persistent Storage
When the file system of the Persistent Storage has errors, Tails now offers you to repair the file system when unlocking from the Welcome Screen.
Because not all file system errors can be safely recovered this way, we wrote comprehensive documentation on how to recover data from the Persistent Storage using complementary techniques.

Changes and updates
Update Tor Browser to 13.5.6.
Improve the notification when a network interface is disabled because MAC address anonymization failed.
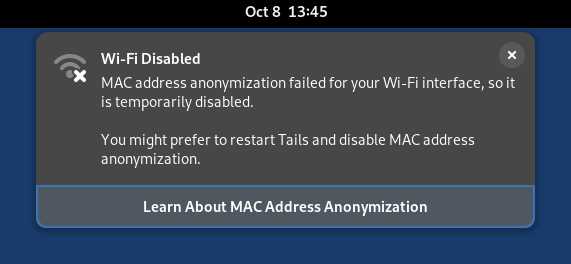
Fixed problems
Increase the maximum waiting time to 8 minutes when unlocking the Persistent Storage before returning an error. (#20475)
Hide shown password while unlocking Persistent Storage. (#20498)
Better handle failures in when sending WhisperBack error messages:
For more details, read our changelog.
Get Tails 6.8
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 6.0 or later to 6.8.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 6.8 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 6.8 directly:
Today the Tor Project, a global non-profit developing tools for online privacy and anonymity, and Tails, a portable operating system that uses Tor to protect users from digital surveillance, have joined forces and merged operations. Incorporating Tails into the Tor Project's structure allows for easier collaboration, better sustainability, reduced overhead, and expanded training and outreach programs to counter a larger number of digital threats. In short, coming together will strengthen both organizations' ability to protect people worldwide from surveillance and censorship.
Pooling resources to better serve a global community
Countering the threat of global mass surveillance and censorship to a free Internet, Tor and Tails provide essential tools to help people around the world stay safe online. By joining forces, these two privacy advocates will pool their resources to focus on what matters most: ensuring that activists, journalists, other at-risk and everyday users will have access to improved digital security tools.
In late 2023, Tails approached the Tor Project with the idea of merging operations. Tails had outgrown its existing structure. Rather than expanding Tails’s operational capacity on their own and putting more stress on Tails workers, merging with the Tor Project, with its larger and established operational framework, offered a solution. By joining forces, the Tails team can now focus on their core mission of maintaining and improving Tails OS, exploring more and complementary use cases while benefiting from the larger organizational structure of The Tor Project.
This solution is a natural outcome of the Tor Project and Tails' shared history of collaboration and solidarity. 15 years ago, Tails' first release was announced on a Tor mailing list, Tor and Tails developers have been collaborating closely since 2015, and more recently Tails has been a sub-grantee of Tor. For Tails, it felt obvious that if they were to approach a bigger organization with the possibility of merging, it would be the Tor Project.
"Running Tails as an independent project for 15 years has been a huge effort, but not for the reasons you might expect. The toughest part wasn't the tech–it was handling critical tasks like fundraising, finances, and HR. After trying to manage those in different ways, I’m really relieved that Tails is now under the Tor Project’s wing. In a way, it feels like coming home."
–intrigeri, Team Lead Tails OS, The Tor Project
Welcoming new users and partners into our communities
Whether it’s someone seeking access to the open web or facing surveillance, Tor and Tails offer complementary protections. While Tor Browser anonymizes online activity, Tails secures the entire operating system–from files to browsing sessions. For journalists working in repressive regions or covering sensitive topics, Tor and Tails are often used as a set to protect their communications and safeguard their sources. The merger will lead to more robust treatment of these overlapping threat models and offer a comprehensive solution for those who need both network and system-level security in high-risk environments.
It will also open up broader training and outreach opportunities. Until now, Tor’s educational efforts have primarily focused on its browser. With Tails integrated into these programs, we can address a wider range of privacy needs and security scenarios. Lastly, this merger will lead to increased visibility for Tails. Many users familiar with Tor may not yet know about Tails OS. By bringing Tails within the Tor Project umbrella, we can introduce this powerful tool to more individuals and groups needing to remain anonymous while working in hostile environments.
"Joining Tor means we’ll finally have the capacity to reach more people who need Tails. We've known for a long time that we needed to ramp up our outreach, but we just didn’t have the resources to do so"
–intrigeri
"By bringing these two organizations together, we’re not just making things easier for our teams, but ensuring the sustainable development and advancement of these vital tools. Working together allows for faster, more efficient collaboration, enabling the quick integration of new features from one tool to the other. This collaboration strengthens our mission and accelerates our ability to respond to evolving threats."
– Isabela Fernandes, Executive Director, The Tor Project
Your support will go a long way to support this merge. Please consider making a donation to the Tor Project
If you'd like to earmark your donation specifically for Tails activities, you can continue to do so through Tails' donation page until further notice.
To learn more about how we are integrating our donation infrastructures and how your funds will be used, please refer to our updated Donation FAQ.
Highlights
In August:
We continued making it easier for Tails users to recover from the most common failure modes:
we released the first iteration of our design to detect a partition table corruption and advise users about it.
we worked on implementing detection of the Persistent Storage corruption on a Tails USB stick, reporting it to users, and repairing it.
We resumed our work to design a better backup feature for the Persistent Storage. We integrated the valuable feedback received in July on our design proposal for the improved backup feature (mockups on Gitlab).
We published instructions for installing Dangerzone in Tails. Dangerzone will help Tails users convert suspicious documents to safe PDFs. This was a significant milestone: this is the first time that we have recommended installing a 3rd party package that is not available in Debian.
Releases
In Tails 6.6, we brought:
improved hardware support for graphics, WiFi etc.
an updated Tor Browser and fixed issues with connecting to the Tor network using default bridges
fixes that make the Persisten Storage more robust.
To know more, check out the Tails 6.6 release notes and the changelog.
Metrics
Tails was started more than 767,542 times this month. That's a daily average of over 24,759 boots.
Changes and updates
Update Tor Browser to 13.5.3.
Update Thunderbird to 115.15.0.
Update OnionShare from 2.2 to 2.6, which includes a feature to create an anonymous chat room.


Fixed problems
Keep the firewall on even during shutdown. (#20536)
Stop reporting an error when starting an old Tails USB stick with a system partition of 2.5 GB. (#20519)
For more details, read our changelog.
Known issues
Shim SBAT verification error
If you get the following error message when starting your regular Linux operating system, then it means that your Linux operating system is outdated.
Verifying shim SBAT data failed: Security Policy Violation
Something has gone seriously wrong: SBAT self-check failed: Security Policy Violation
Edit your UEFI settings to disable Secure Boot.
With Secure Boot disabled, your regular Linux operating system should start again.
To learn how to edit the BIOS or UEFI settings, search for the user manual of the computer on the support website of the manufacturer.
Update your regular Linux operating system.
Try to enable Secure Boot again in your UEFI settings.
If your regular Linux operating system still doesn't start, then disable Secure Boot again. You can try to enable Secure Boot again in the future.
It might take several months for your Linux distribution to provide updates before you can enable Secure Boot again.
Get Tails 6.7
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 6.0 or later to 6.7.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 6.7 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 6.7 directly:
Highlights
On our first month back from vacation, we continued making it easier to recover from common failure modes without requiring technical expertise:
we drafted an implementation of our design to detect, report, and repair corruption of the Persistent Storage
we finished implementing our plans to improve the detection of and recovery from low-memory situations. Going from prototype to implementation, this work was a great example of the 90-90 rule in action: the first 90% of the work consumed the first 90% of our time, and the remaining 10% accounted for the other 90% of our time
Over the past year, we have been close downstream of the Tor Project's design and implementation of Arti. This month, we reached a significant milestone in our collaboration: we prepared a prototype of Tails in which multiple applications use Arti.
freiheitsfoo, one of our longest supporters, renewed their sponsorship of Tails! Welcome aboard for another year of resisting censorship and surveillance online!
Releases
In Tails 6.5, we brought:
an updated Tor Browser with cool letterboxing improvements, and the latest Debian (12.6)
repairs to first-boot partitioning that many users were facing issues with after Tails 6.4
fixes to connecting via mobile broadband, LTE, and PPPoE DS. This has been a persistent issue in the Tails 6 series so far.
To know more, check out the Tails 6.5 release notes and the changelog.
Metrics
Tails was started more than 779,262 times this month. That's a daily average of over 25,946 boots.
Changes and updates
Update Tor Browser to 13.5.2.
Update Thunderbird to 115.14.0.
Update many firmware packages. This improves the support for newer hardware: graphics, Wi-Fi, and so on.
Detect new types of errors when resizing the system partition fails (the first time Tails is started) and report the following error message.
Something went wrong when starting your Tails USB stick for the first time:
resizing the system partition failed
It will be impossible to create a Persistent Storage or apply automatic upgrades.Affected users can try to install Tails again or use a different USB stick.
Fixed problems
Persistent Storage
Increase the maximum waiting time to 4 minutes when unlocking the Persistent Storage before returning an error. (#20475)
Made the creation of the Persistent Storage more robust after starting a Tails USB stick for the first time. (#20451)
Prevent the Persistent Storage settings from freezing after opening a link to the documentation. (#20438)
Prevent Additional Software from crashing when installing virtual packages. (#20477)
Networking
Fix connecting to the Tor network using default bridges. (#20467)
Allow enabling multiple network interfaces again. (#20128)
Tails Cloner
- Remove 30 seconds of waiting time when installing by cloning. (#20131)
For more details, read our changelog.
Get Tails 6.6
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 6.0 or later to 6.6.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 6.6 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 6.6 directly:
Today, we added documentation on our website to install Dangerzone in Tails.
When you receive untrusted documents, for example, email attachments, Dangerzone allows you to convert them into safe PDFs before opening.
Dangerzone is particularly useful for journalists who might receive dangerous documents from anonymous sources or download them from the Internet.
Dangerzone is an essential tool and is built by great people. It was first written by Micah Lee to protect investigative journalists while working at The Intercept. Dangerzone is now maintained by Freedom of the Press Foundation, a non-profit that protects public-interest journalism. Edward Snowden and Laura Poitras are on its Board of Directors.
It's totally the kind of software that aligns with our mission. The only reason why we are not including Dangerzone in Tails by default is because Dangerzone is too big and not available in Debian.
So, we collaborated with Alex Pyrgiotis from Freedom of the Press Foundation to make it as easy as possible to install Dangerzone in Tails as Additional Software. The setup requires using the command line, but, after that, Dangerzone will install automatically every time you start Tails.
Dangerzone will allow more investigative journalists to use the safe environment that Tails provides when manipulating sensitive documents.
It's also the first time that we recommend installing a 3rd party package that is not available in Debian. We know that a lot of software that would be useful for our users is not readily available in Debian. If this first experiment is successful, we might document more such packages.
Changes and updates
Make installation with Tails Cloner 30 seconds faster. (!1588)
Update Tor Browser to 13.5.1, including improved letterboxing.
Update Debian to 12.6.
Fixed problems
Fix preparation for first use often breaking legacy BIOS boot and creation of Persistent Storage. (#20451)
Fix language of Tor Browser when started from Tor Connection. (#20318)
Fix connection via mobile broadband, LTE, and PPPoE DSL. (#20291, #20433)
For more details, read our changelog.
Known issues
It is impossible to connect using the default Tor bridges already included in Tails. (#20467)
To use a default bridge in Tails 6.5, scan the QR code of one of these bridges:


If this fails, configure a custom bridge.
Get Tails 6.5
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 6.0 or later to 6.5.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 6.5 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 6.5 directly:
